Archive
Managing macOS Catalina’s FileVault 2 with fdesetup
Since its initial release in OS X Mountain Lion 10.8.x, Apple’s main tool for managing FileVault 2 encryption has been fdesetup. With the transition from managing Core Storage-based encryption on HFS+ to managing the native encryption built into Apple File System completed, this well-developed toolset continues to be Apple’s go-to tool for enabling, configuring and managing FileVault 2 on macOS Catalina.
With its various functions, fdesetup gives Mac administrators the following options for managing FileVault:
- Enable or disable FileVault 2 encryption on a particular Mac
- Use a personal recovery key, an institutional recovery key, or both kinds of recovery key.
- Enable one or multiple user accounts at the time of encryption
- Get a list of FileVault 2-enabled users on a particular machine
- Add additional users after FileVault has been enabled
- Remove users from the list of FileVault enabled accounts
- Add, change or remove individual and institutional recovery keys
- Report which recovery keys are in use
- Perform a one-time reboot that bypasses the FileVault pre-boot login
- Report on the status of FileVault 2 encryption or decryption
For more details, please see below the jump.
Managing macOS Mojave’s FileVault 2 with fdesetup
Since its initial release in OS X Mountain Lion 10.8.x, Apple’s main tool for managing FileVault 2 encryption has been fdesetup. With the transition from managing Core Storage-based encryption on HFS+ to managing the native encryption built into Apple File System completed, this well-developed toolset continues to be Apple’s go-to tool for enabling, configuring and managing FileVault 2 on macOS Mojave.
With its various functions, fdesetup gives Mac administrators the following options for managing FileVault:
- Enable or disable FileVault 2 encryption on a particular Mac
- Use a personal recovery key, an institutional recovery key, or both kinds of recovery key.
- Enable one or multiple user accounts at the time of encryption
- Get a list of FileVault 2-enabled users on a particular machine
- Add additional users after FileVault has been enabled
- Remove users from the list of FileVault enabled accounts
- Add, change or remove individual and institutional recovery keys
- Report which recovery keys are in use
- Perform a one-time reboot that bypasses the FileVault pre-boot login
- Report on the status of FileVault 2 encryption or decryption
For more details, please see below the jump.
Unlock or decrypt your FileVault-encrypted boot drive from the command line on macOS Mojave
As part of working with FileVault on macOS Mojave, it may be necessary to decrypt an encrypted boot drive in order to fix a problem. On Mojave all boot volumes will use Apple File System (APFS), so to unlock or decrypt an encrypted boot drive from the command line, you will need to do the following:
- Identify the relevant encrypted APFS volume
- Unlock the encrypted APFS volume
- If needed, decrypt the encrypted APFS volume
For more details, see below the jump.
Cancelling an unwanted FileVault deferred enablement
There are sometimes occasions when FileVault deferred encryption has been enabled for a particular Mac and then needs to be turned off. Since FileVault is not yet turned on at this point, there is no obvious way to turn off this deferred enablement.
However, it is possible to turn off a deferred enablement if needed. For more details, please see below the jump.
Slides from the “Managing FileVault 2 on macOS High Sierra” Session at MacAD UK 2018 Conference
For those who wanted a copy of my FileVault 2 management talk at MacAD UK 2018, here are links to the slides in PDF and Keynote format.
PDF – http://tinyurl.com/MacADUK2018pdf
Keynote – http://tinyurl.com/MacADUK2018key
Hat tip to the attendee who brought to my attention that fdesetup sync is not supported on encrypted APFS boot drives. I’ve now updated the slides to reflect that it works on macOS High Sierra for HFS+ drives only.
HFS+

APFS

Using FileVault 2 recovery keys on FileVault 2-encrypted Macs to provide access for local admins
It can be difficult to provide consistent access for Mac admins when using a local admin account on FileVault 2-encrypted Macs, due to the way password changes are handled for FileVault 2-enabled accounts. The reason for the difficulty is that FileVault 2’s encryption doesn’t care about passwords, it only cares about encryption keys.
When an account on a particular Mac is enabled for FileVault 2, the account’s password is used to generate an key which can be used to unlock the encrypted Core Storage volume that FileVault 2 sets up on the Mac. When the password for the enabled account gets changed, the password and its associated key are updated by first requesting the previous password (and its associated key) to authenticate the change to the new password and associated key.
Assuming that the old password is provided as part of the password change process, no problem. However, if the old password is not provided as part of the password change process, the new password does not get an associated key to unlock FileVault 2 because the old password’s key was not invoked to authorize the change to a new key. The result of this is that the new password can be used to log into the OS and provide whatever password authorization duties are needed for the OS, but you still need the account’s old password to log into the Mac at the FileVault 2 login screen.
The usual fix for this situation is to run the following commands with root privileges:
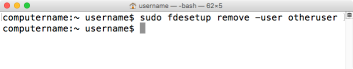
1. Remove the user from the list of FileVault 2-enabled accounts
fdesetup remove -user username_goes_here
2. Add the user back to the list of FileVault 2-enabled accounts
fdesetup add -usertoadd username_goes_here

When the account is re-enabled using the fdesetup add -usertoadd command, a new key is set up for the user and the passwords are back in sync. However, there are two drawbacks to this approach if a Mac admin wants to automate this:
- You need to provide the password in a non-encrypted format of the account being enabled.
- You need to provide in a non-encrypted format either a recovery key or the password of another FV 2-enabled account on the Mac.
In short, the passwords and/or recovery key used to remove and re-enable the account in question need to be provided “in the clear”, where anyone successfully intercepting the passwords will be able to read them.
Fortunately, for those Mac admins who have a way to capture and escrow FileVault 2 personal recovery keys, there is an alternative to enabling the local admin account. For more details, see below the jump.
fdesetup authrestart no longer requires an immediate restart in macOS Sierra
Apple made a change to the fdesetup authrestart command in macOS Sierra, where running fdesetup authrestart will no longer require the encrypted Mac in question to restart immediately.
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| authrestart [-inputplist] [-delayminutes number_of_minutes_to_delay] [-verbose] | |
| If FileVault is enabled on the current volume, it restarts the system, | |
| bypassing the initial unlock. The optional -delayminutes option can | |
| be used to delay the restart command for a set number of minutes. A | |
| value of 0 represents 'immediately', and a value of -1 represents | |
| 'never'. The command may not work on all systems. |
The delayed restart option can be enabled by adding the -delayminutes verb to the fdesetup authrestart command and specifying one of the following:
- Time in minutes = Delay the restart command for a set number of minutes
- 0 = immediate restart
- -1 = wait indefinitely for restart
Using the -1 option means that the user can restart at their convenience and their encrypted Mac will automatically bypass the FileVault 2 pre-boot login at the next reboot.
To show what this behavior looks like, please see the videos below:
fdesetup authrestart -delayminutes 0
fdesetup authrestart -delayminutes 0
Note: The video has been edited to artificially reduce the amount of time the restart process takes to run. Run time of the pre-edited video was 1 minute 30 seconds.
fdesetup authrestart -delayminutes 1
fdesetup authrestart -delayminutes 1
Note: The video has been edited to artificially reduce the amount of time the restart process takes to run. Run time of the pre-edited video was 2 minutes 18 seconds.
fdesetup authrestart -delayminutes -1
fdesetup authrestart -delayminutes -1
Note: The video has been edited to artificially reduce the amount of time the restart process takes to run. Run time of the pre-edited video was 1 minute 43 seconds.
Identifying FileVault 2 institutional recovery keys on OS X El Capitan
On OS X 10.9.0 – 10.11.x, you can run the following command to verify if a FileVault 2-encrypted Mac is using an institutional recovery key (IRK) as a valid recovery key.
fdesetup hasinstitutionalrecoverykey
If FileVault 2 is using an IRK, this command will return true.

Otherwise it will return false.

As part of the release of OS X 10.11.2, a new function was added to fdesetup‘s hasinstitutionalrecoverykey verb. Now, in addition to identifying whether or not FileVault 2 on a particular Mac has an institutional recovery key, a new -device option has been added which outputs a SHA-1 hash in hexadecimal notation of the IRK’s public key. This helps Mac admins answer two questions about institutional recovery keys:
- Is an IRK being used as a valid recovery key on this Mac?
- If an IRK is in use, which one is being used?
The -device option needs to be supplied with an identifier for the encrypted drive in question. This can be in the form of a BSD device name ( /dev/diskX ), the mount path ( /Volumes/Macintosh HD or / ), or a UUID for the Logical Volume or Logical Volume Family of a CoreStorage volume.
To display the hash for an IRK’s public key on the Mac’s boot volume, run the command below with root privileges:
fdesetup hasinstitutionalrecoverykey -device /
It should output the hash of the IRK’s public key in hexadecimal notation.

This value should be consistent across all FileVault 2-encrypted Macs which are using this IRK, so it should help Mac admins identify if a particular Mac is set up with the correct FileVault 2 institutional recovery key (or keys) used by their shop.
To assist with this, I’ve written a script to report the hash of the IRK’s public key. For more details, see below the jump.
Managing El Capitan’s FileVault 2 with fdesetup
For the first time since fdesetup‘s initial release in OS X Mountain Lion 10.8.x, Apple has not added new features to fdesetup as part of a new OS release. Instead, fdesetup maintains the same set of features in OS X El Capitan 10.11.x as it had in OS X Yosemite 10.10.x.
This decision may mean that fdesetup, an essential command-line tool for enabling, administering and disabling Apple’s FileVault 2 encryption, is now considered by Apple to be a fully-developed toolset for managing FileVault 2.
fdesetup gives Mac administrators the following command-line abilities:
- Enable or disable FileVault 2 encryption on a particular Mac
- Use a personal recovery key, an institutional recovery key, or both kinds of recovery key.
- Enable one or multiple user accounts at the time of encryption
- Get a list of FileVault 2-enabled users on a particular machine
- Add additional users after FileVault has been enabled
- Remove users from the list of FileVault enabled accounts
- Add, change or remove individual and institutional recovery keys
- Report which recovery keys are in use
- Perform a one-time reboot that bypasses the FileVault pre-boot login
- Report on the status of FileVault 2 encryption or decryption
I’ll be taking you through all of the capabilities mentioned above, with a focus on showing exactly how they work. See below the jump for details.
Managing Yosemite’s FileVault 2 with fdesetup
With the release of Yosemite, Apple has continued to add functionality to fdesetup, a valuable command-line tool for enabling, administering and disabling Apple’s FileVault 2 encryption. This tool gives Mac administrators the following command-line abilities:
- Enable or disable FileVault 2 encryption on a particular Mac
- Use a personal recovery key, an institutional recovery key, or both kinds of recovery key.
- Enable one or multiple user accounts at the time of encryption
- Get a list of FileVault 2-enabled users on a particular machine
- Add additional users after FileVault has been enabled
- Remove users from the list of FileVault enabled accounts
- Add, change or remove individual and institutional recovery keys
- Report which recovery keys are in use
- Perform a one-time reboot that bypasses the FileVault pre-boot login
- Report on the status of FileVault 2 encryption or decryption
I’ll be taking you through all of the capabilities mentioned above, with a focus on showing exactly how they work. See below the jump for details.
Recent Comments