Archive
Suppressing the iCloud and Diagnostics pop-up windows on El Capitan using profiles
After posting how to control the Diagnostics & Usage report settings on El Capitan, I was tipped off that there were new ways available on OS X El Capitan to manage both the Diagnostics and the iCloud pop-up windows using profiles.
The profile settings can be seen via Server 5.x’s Profile Manager and currently apply only to OS X El Capitan. For more information, see below the jump.
Controlling the Diagnostics & Usage report settings on El Capitan
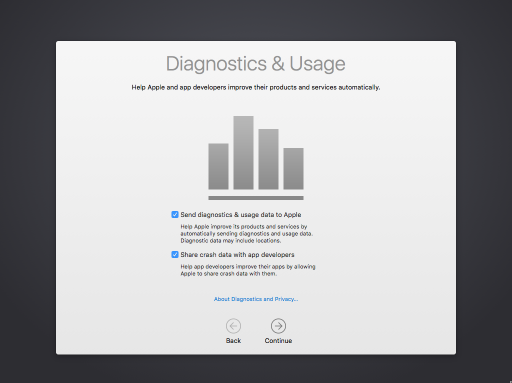
One of the pop-up windows you get on first login to Yosemite and El Capitan is the Diagnostics & Usage pop-up window. This window requests permission for the following:
- Send diagnostics and usage data to Apple
- Share crash data with non-Apple developers
I’ve been suppressing this window on OS X Yosemite by setting the values shown below in /Library/Application Support/CrashReporter/DiagnosticMessagesHistory.plist
<key>AutoSubmitVersion</key> <integer>5</integer> <key>AutoSubmit</key> <false/> <key>ThirdPartyDataSubmitVersion</key> <integer>5</integer> <key>ThirdPartyDataSubmit</key> <false/>
On OS X El Capitan, it looks like the numeric value set for the AutoSubmitVersion and ThirdPartyDataSubmitVersion settings has changed from 4 to 5. The new settings should look like this:
<key>AutoSubmitVersion</key> <integer>5</integer> <key>AutoSubmit</key> <false/> <key>ThirdPartyDataSubmitVersion</key> <integer>5</integer> <key>ThirdPartyDataSubmit</key> <false/>
For more details, see below the jump.
Payload-free package slides from the January 2016 MacDMV meeting
For those who wanted a copy of the payload-free package talk from this evening’s MacDMV meeting, here are links to the slides in PDF and Keynote format:
PDF: http://tinyurl.com/Jan2016MacDMVPDF
Keynote slides: http://tinyurl.com/Jan2016MacDMVKeynote
Suppressing Office 2016’s First Run dialog windows
As part of preparing to deploy Office 2016 in my own environment, I wanted to be able to suppress the various “What’s New” dialog windows which are displayed on Office 2016 applications’ first launch to market the applications’ features.

Using the Microsoft Volume License installer to install Office 2016 (or using the volume license serializer package to install the volume license) will include automatic functionality to stop the version-specific “What’s New” dialog windows from appearing. However, I also needed to be able to suppress the initial “What’s New” dialog windows that appear the first launch of Office applications.
In order to suppress the initial “What’s New” dialog windows, certain settings need to be applied to the following files:
- /Library/Preferences/com.microsoft.Outlook.plist
- /Library/Preferences/com.microsoft.PowerPoint.plist
- /Library/Preferences/com.microsoft.Excel.plist
- /Library/Preferences/com.microsoft.Word.plist
- /Library/Preferences/com.microsoft.onenote.mac.plist
Setting: kSubUIAppCompletedFirstRunSetup1507 – boolean value (true / false)
Function: Suppresses the “What’s New” dialog for Office 2016 applications’ first launch.
Applied to the following files:
/Library/Preferences/com.microsoft.Outlook.plist
/Library/Preferences/com.microsoft.PowerPoint.plist
/Library/Preferences/com.microsoft.Excel.plist
/Library/Preferences/com.microsoft.Word.plist
/Library/Preferences/com.microsoft.onenote.mac.plist
Setting: FirstRunExperienceCompletedO15 – boolean value (true / false)
Function: Suppresses additional “What’s New” dialog for Outlook and OneNote.
Applied to the following files:
/Library/Preferences/com.microsoft.Outlook.plist
/Library/Preferences/com.microsoft.onenote.mac.plist
Note: That is a capital letter O in O15, not zero15.
Setting: SendAllTelemetryEnabled – boolean value (true / false)
Function: Suppresses the offer to send crash reports to Microsoft.
Applied to the following files:
/Library/Preferences/com.microsoft.Outlook.plist
/Library/Preferences/com.microsoft.PowerPoint.plist
/Library/Preferences/com.microsoft.Excel.plist
/Library/Preferences/com.microsoft.Word.plist
/Library/Preferences/com.microsoft.onenote.mac.plist
To automate the deployment of these settings, I’ve developed a script. For more details, see below the jump.
Creating an Office 2016 15.18.0 installer
Microsoft recently released a new software installer to help make the task of deploying updated copies of Office 2016 for Mac admins a lot easier. This new installer is available along with the latest Office 2016 volume license installer and is named Microsoft_Office_2016_VL_Serializer.pkg.

This installer is designed to do the following:
- Activate an unlicensed version of Office 2016 and set it to use the volume license.
- Convert an existing/activated version of Office 2016 for Mac to use the volume license.
- Fix the volume license on a machine where the volume license isn’t being recognized.
The installer package (which must be downloaded from Microsoft’s volume license site) makes it possible to install an unlicensed copy of the Microsoft Office 2016 full installer and then set up that copy of Office 2016 to use your shop’s volume license for Office 2016. This is advantageous for the following reasons:
- Microsoft usually releases unlicensed Office 2016 full installers much sooner than they release the volume licensed Office 2016 full installer via Microsoft’s volume license site.
- Unlicensed Office 2016 full installers can be downloaded from the internet without requiring access to Microsoft’s volume licensing site.
For example, as of January 14, 2016, the latest version of Office 2016 is Office 2016 15.18.0. Microsoft has released an unlicensed Office 2016 15.18.0 full installer for use with Office 365. Meanwhile, the Microsoft volume license site site has Office 2016 15.17.0 available for download.
Downloading an unlicensed Office 2016 full installer
- Go to http://macadmins.software (this site is run by Microsoft and is safe to download from.)
- Locate the O365/Retail download link (highlighted in bright green in the image below.)
- Download an unlicensed Office 2016 full installer which is up-to-date with the latest Office 2016 software

I have an existing process which can be used to build a combined Office 2016 installer using Packages, so I decided to apply the same process to building an Office 2016 15.8.0 installer. See below the jump for an example of using Packages to build a combined Office 2016 installer which includes both an unlicensed Office 2016 15.18.0 full installer and the Microsoft_Office_2016_VL_Serializer installer package.
FIPS 140-2 validation and FileVault 2
One question I’ve seen which has caused confusion for folks who deal with security regulations is this: Is FileVault 2 FIPS 140-2 compliant?
The answer is: Yes, depending on the version of OS X
The cryptography used by FileVault 2 on the following versions of OS X has gone through the FIPS validation process and has been validated as being FIPS 140-2 Compliant:
The CoreCrypto cryptographic modules used by OS X 10.11 are currently in the process of becoming FIPS 140-2 validated. The reason FileVault 2 in El Capitan is not automatically FIPS 140-2 compliant has to do with OS X’s CoreCrypto cryptography foundation and how the FIPS 140-2 validation process works.
FIPS validation
The FIPS validation process tests a specific cryptographic module used inside a system to protect information. It also applies only to a cryptographic module used in a shipping product; the cryptographic module in question can’t be a prototype or in beta.
Another important thing to know is that the testing is very specific and applies only to the cryptographic module submitted for review. If the vendor changes anything in the cryptographic module, it loses its FIPS validation and has to be resubmitted for laboratory testing and government review.
There are three major phases in the process:
Phase 1: Design and Documentation
In order to prepare for the FIPS validation process, the cryptographic module in question has to be designed to pass the various tests involved and also be properly documented. This is the part of the process which the vendor has the most control over.
Phase 2: Laboratory Testing
Once the cryptographic module has been designed, documented and shipped, it is submitted to a third-party accredited Cryptographic and Security Testing (CST) laboratory to test the module(s) in question against FIPS 140-2’s qualitative levels of security. This testing can take an indeterminate amount of time, depending on how well the cryptographic module is designed and documented.
Best case: A cryptographic module that properly meets the requirements and with all required documentation written correctly can complete its laboratory testing in two to three months.
Phase 3: Government Review
After the lab has tested the cryptographic module, a report on the testing is submitted to the Cryptographic Module Validation Program (CMVP) for review. CMVP is a joint US-Canadian program that reviews all the test reports, with the CMVP Validation Authorities being the National Institute of Standards and Technology (NIST) for the US Government and the Communications Security Establishment (CSE) for the Government of Canada. This review can also take an indeterminate amount of time, depending on how many test reports need review, and can range from two months to eight months.
Apple and CoreCrypto
Apple’s CoreCrypto library is used by various components in OS X to provide low level cryptographic primitive support. This is the cryptographic library which is submitted by Apple to the FIPS 140-2 validation process.
With every version of iOS and OS X, Apple has made changes to CoreCrypto. As part of making those changes, Apple has had to resubmit CoreCrypto to laboratory testing and government review as part of the FIPS 140-2 validation process.
Apple’s stated intention is to continue FIPS 140-2 validation for OS X’s CoreCrypto cryptography foundation, which would also cover FileVault 2 on future versions of OS X, but the validation process itself can only be begun once that future OS has been released. Meanwhile, as noted above, the testing and governmental review process will take months to complete.
The good news is that it’s possible to at least see where Apple is in the process. NIST has a website where the current list of modules in the process can be viewed via a PDF which is updated weekly. To check for Apple’s progress, search the PDF for entries where Apple Inc. is listed as the vendor.
For more information on this subject, Apple has KBase articles available via the links below:
Product security, validations, and guidance for iOS
Product security, validations, and guidance for OS X
Apple’s existing FIPS validations are also available for reference via the link below:
http://csrc.nist.gov/groups/STM/cmvp/documents/140-1/1401vend.htm
First look at Veertu
One of the lesser-known changes that Apple introduced with OS X Yosemite was a Hypervisor framework, which was designed to allow virtualization solutions to be built for OS X without the need for third-party kernel extensions.

One reason for this was that eliminating the need for kernel extensions allowed the possibility of virtualization software to be distributed and sold via the Mac App Store. While neither VMware or Parallels have taken advantage of this, a new virtualization product named Veertu has recently become available in the MAS.

Veertu is available for free from the MAS, and allows installation of selected Linux VMs, downloaded from Veertu’s online library. For more details, see below the jump.
Recent Comments