Unlock or decrypt your FileVault-encrypted boot drive from the command line on macOS Mojave
As part of working with FileVault on macOS Mojave, it may be necessary to decrypt an encrypted boot drive in order to fix a problem. On Mojave all boot volumes will use Apple File System (APFS), so to unlock or decrypt an encrypted boot drive from the command line, you will need to do the following:
- Identify the relevant encrypted APFS volume
- Unlock the encrypted APFS volume
- If needed, decrypt the encrypted APFS volume
For more details, see below the jump.
Identifying the encrypted APFS volume
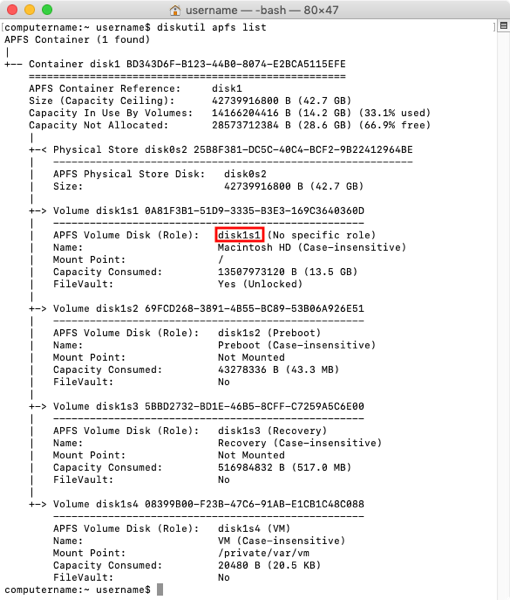
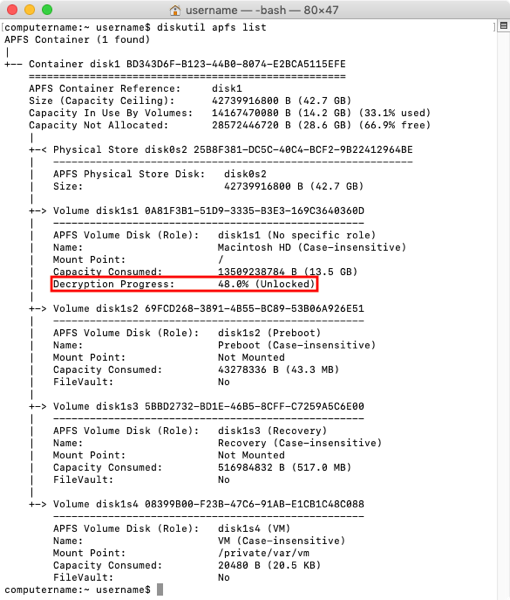
A necessary pre-requisite to unlocking APFS encryption is to identify the correct encrypted volume. To do this, open Terminal and run the following command:
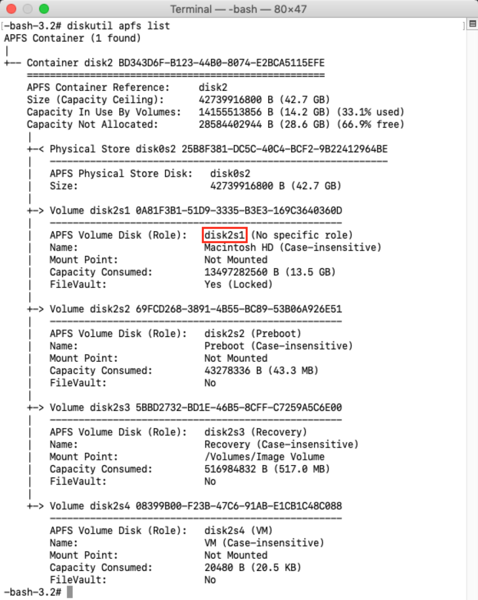
diskutil apfs list
Running that command will give you a listing of all APFS containers and volumes. To help identify what you’re looking for, I’ve highlighted the identifier of the encrypted APFS volume in this example:
Unlocking the encrypted APFS volume
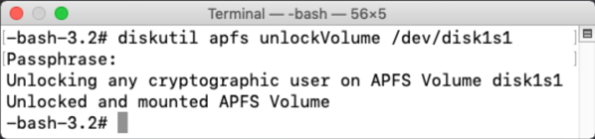
If you have access to the password of one of the enabled accounts on the encrypted APFS volume, you can unlock using the command shown on the screen. You will be prompted to provide the password.
diskutil apfs unlockVolume /dev/apfs_volume_id_goes_here
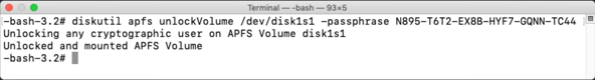
If you have access to the personal recovery key associated with the encrypted APFS volume, you can unlock using the command shown on the screen. You will need to provide the recovery key as part of the command.
diskutil apfs unlockVolume /dev/apfs_volume_id_goes_here -passphrase personal_recovery_key_goes_here
If using an institutional recovery key, you can unlock the encryption using a FileVaultMaster keychain that contains both the public and private key of your institutional recovery key. One requirement is that you will need to be booted from a Recovery HD partition or from Internet Recovery. Here’s how to do this:
1. Copy the FileVaultMaster keychain that contains both the public and private key of your institutional recovery key to a drive that you can access from Recovery HD.
2. Boot to Recovery HD.
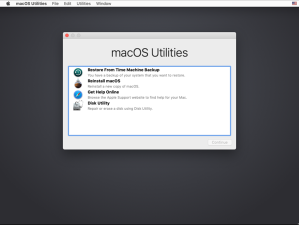
3. Open Terminal.
4. Get the APFS volume ID of the encrypted drive by running the following command:
diskutil apfs list
5. With the APFS volume ID information acquired, run the following command to unlock the FileVaultMaster.keychain:
security unlock-keychain /path/to/FileVaultMaster.keychain
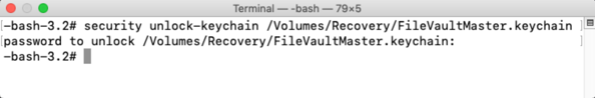
Once this command is run, you’ll need to enter the keychain’s password when prompted. If the password is accepted, you’ll be taken to the next prompt.
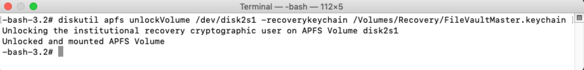
6. Run the following command to unlock the encrypted APFS volume on the encrypted Mac:
diskutil apfs unlockVolume /dev/apfs_volume_id_goes_here -recoverykeychain /path/to/FileVaultMaster.keychain
7. You should then see output similar to the following:
Decrypting the encrypted APFS volume
Once the drive has been unlocked, you can then decrypt the APFS volume. In order to decrypt using a user account’s password or a recovery key, it is necessary to specify the following:
- The relevant encrypted APFS volume
- The relevant user UUID, unless using an institutional recovery key.
- The relevant account password, personal recovery key or institutional recovery key.
If you are planning to use a user account’s password to decrypt, you will first need to correctly identify the relevant encrypted APFS volume and which UUID you want to use. The encrypted APFS volume must also be unlocked and ready for decryption
You can get the UUID of a user account by running the command shown below and matching which UUID belongs to the account you want to use.
fdesetup list
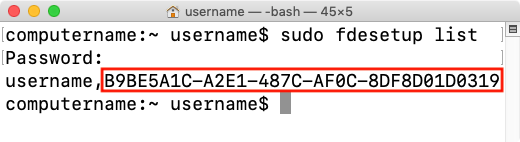
If you are not booted from the encrypted drive, there is another way to get the UUID but it does not include the account name.
diskutil apfs listcryptousers /dev/apfs_volume_id_goes_here
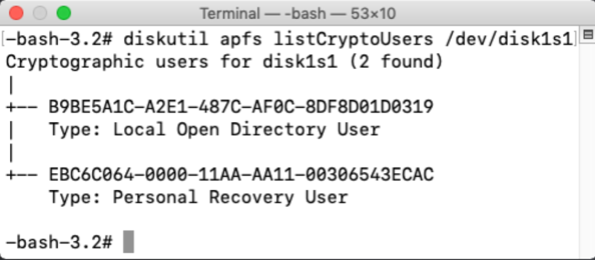
In this case, use the UUID associated with the Local Open Directory User entry.
Unfortunately, this may lead to some guesswork on your part if there is more than one FileVault enabled account enabled. With multiple accounts enabled, there will be will be multiple Local Open Directory User entries.
Decrypting using an account password:
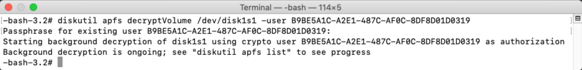
Once you have access to the UUID and password of one of the enabled accounts on the encrypted APFS volume, you can decrypt using the command below. You will be prompted to provide the password:
diskutil apfs decryptVolume /dev/apfs_volume_id_goes_here -user uuid_goes_here
Decrypting using a personal recovery key:
If you want to use the personal recovery key, the PRK has its own UUID which only appears if you run the following command:
diskutil apfs listcryptousers /dev/apfs_volume_id_goes_here
In this case, use the UUID associated with the Personal Recovery User entry.
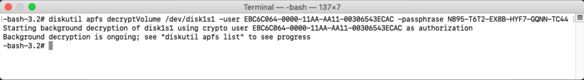
If you have access to the personal recovery key associated with the encrypted APFS volume, you can decrypt using the command below. You will need to provide the relevant UUID and the alphanumeric recovery key as part of the command.
diskutil apfs decryptVolume /dev/apfs_volume_id_goes_here -user uuid_goes_here -passphrase personal_recovery_key_goes_here
Decrypting using an institutional recovery key:
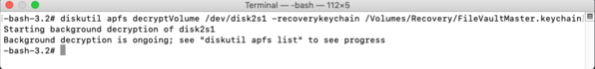
If you want to use the institutional recovery key, decryption using an IRK does not require the use of UUIDs. Instead, once the recovery key and the encrypted drive have both been unlocked, you can decrypt using the command shown below.
diskutil apfs decryptVolume /dev/apfs_volume_id_goes_here -recoverykeychain /path/to/filename_here.keychain
Monitoring decryption
You can monitor decryption of the APFS volume from the command line by running the following command:
diskutil apfs list
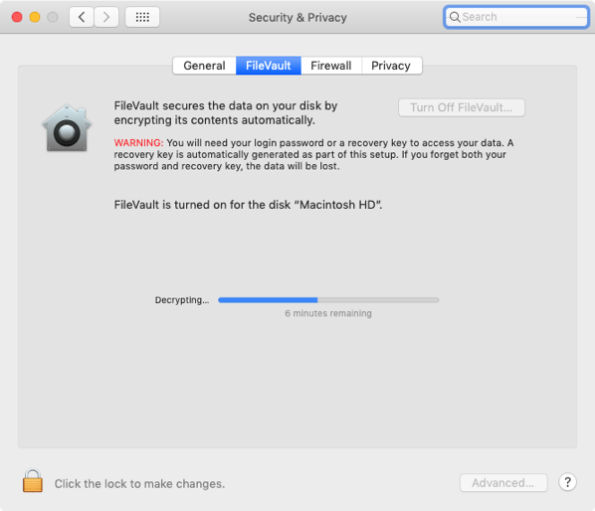
You can also monitor it via the following means:
- Boot from the decrypting drive.
- Open System Preferences
- Open the Security & Privacy preference pane
- Click the FileVault tab
- View the current decryption status
Will this also work if the encryption was done with the user’s iCloud account?
Cryptographic users for disk1s1 (4 found)
|
+– 7251A7A3-7B33-440E-9A65-A85AD5629F8F
| Type: Local Open Directory User
|
+– EC1C2AD9-B618-4ED6-BD8D-50F361C27507
| Type: iCloud Recovery User
|
+– 64C0C6EB-0000-11AA-AA11-00306543ECAC
| Type: iCloud Recovery External Key
|
+– E9327782-4A9C-4F16-B488-4113785E6DA0
Type: Local Open Directory User
Hi, did you ever figure this out? Im stuck on prohibited screen and is locked with iCloud aswell. Tried several passphrases that arent working.
I don’t get access to terminal… since filevault is on, and it wont take my password 😦
I’m also still trying to unlock & decrypt using iCloud
Hi, i was able to unlock it.
What you need to do is the following:
1. Enter recovery mode (CMD + R)
2. Open terminal
3. Enter “resetpassword”
4. Wait for the reset password dialogue to open.
5. Chose “I forgot my password” and go through the dialogue. When you are at the end, DO NOT restart the computer. Go in the left corner and click Disk Utility.
6. The disk is now open. You CMD + Q the DIsk Utility window and reinstall the OS if desired.
Sir, as always many, many thanks. I owe you a 6 pack of diet Cokes.
Gracias
So what do I do if there are multiple volumes?
MedTekni you saved my day (after a day trying to unlock the disk) I could not even enter the password when trying to ‘activate’ a partition through disk utility.
This has saved me multiple times, but lately I’ve been seeing computers requiring an admin password to open Terminal, which is a serious problem if I don’t have a password to enter. I’ve tried entering the individual recovery key in the password field (all caps, including dashes) with no luck. In these cases is there a way to mount the disk or change the password using the recovery key?
Mentioned this on another deflounder post, but thought I’d mention it here. These instructions are gold (for instituitional recovery key), but in Catalina the recovery mode doesn’t have a terminal in “recovery assistant”. I couldnt get past this. Apple support couldn’t get past this. Had to create mojave bootable USB, boot that (option key after power on) and use that terminal to unload/decrypt the drive. Apple hasn’t thought this through!
Thank you very much for this very useful & informative post!
Best,
Panos Tsapralis,
IT engineer,
London – UK.
Hi guys!
To decrypt your hackintosh’s drive – you have two options.
FIRST WAY:
You need install FileVault drivers into your EFI configuration, use this instruction below!
https://ihackline.com/2020/10/05/filevault-hackintosh/
You have to made some changes to ENABLE natively FileVault on hackintosh to use your drive encryption normally.
SECOND WAY:
USE your RECOVERY partition to start decrypting process.
0) BOOT INTO RECOVERY PARTITION (cmd+R when booting) or load into clean system from external drive:
1) open terminal from recovery utilities
2) FOR APFS DRIVE type:
/usr/libexec/apfsd
OR TRY THAT!
sudo /usr/libexec/apfsd
FOR HFS DRIVE:
/usr/libexec/corestoraged
OR TRY THAT!
sudo /usr/libexec/corestoraged
3) TO RESUME/START decrypt/encrypt SERVICE of your drive:
OPEN NEW terminal’s window.
4) TYPE:
diskutil apfs list
see your main drive disk0s0 (for example) and write its UUID
5) TYPE:
diskutil apfs listcryptousers /dev/disk0s0
see your username
6) TYPE:
diskutil apfs decryptVolume /dev/disk0s0 -user uuid_goes_here -passphrase 1234567890
Remember!
“1234567890” – is your password of user
“uuid_goes_here” – UUID of your drive
“disk0s0” – your drive partition
7) Check your decrypting status:
diskutil apfs list
P.S. Decryption will be very long. Even if it’s an SSD. Most importantly, check that the decryption percentages are slowly but increasing.
Good luck!
my mbp wont allow me to log in after big sur update…. it does not accept password and says filevault enabled. So I’m locked out. It does not allow me to open terminal in recovery as terminal requires a password also… I’m trying everything I can’t find, can’t figure it out… 😦
You are a KING!
Your article saved me.
I don’t get access to terminal , since filevault is on, and it wont take my password
I don’t get access to termina, since filevault is on, and it wont take my password