Enabling users for FileVault 2 with a non-enabled admin user does not work in Mavericks
Over the past few months, I’ve told hundreds of people the following information about fdesetup in Mountain Lion:
“Once the Mac has been fully encrypted with FileVault 2, you can add additional users using fdesetup. To do so, you will need to provide both the username and password of either a previously enabled account or an admin account, as well as the password of the account you want to add.
There’s something that’s interesting to know about this method: the admin user in question does not themselves need to be enabled for FileVault 2. In my testing, I found that an admin user can authorize the enabling of other accounts even if the admin account wasn’t enabled. An admin account can also enable itself using this process, by being both the authorizing admin account and the account being enabled. This is similar to the System Preferences behavior, where an admin account could enable itself by logging in and clicking the lock in the FileVault preference pane.
Since a key has to be involved somewhere, I’ve got an inquiry open with Apple as to why this works but I haven’t heard back yet.”
I’ve now heard back. See below the jump for the details.
Mountain Lion
In Mountain Lion, once FileVault 2 is enabled, fdesetup uses the keys which become available after the volume is unlocked. It prompts for credentials in case those keys are no longer available. This was how non-enabled admin users were able to enable other non-enabled users; fdesetup had access to the needed key.
In the case of the example below, fv2admin is a non-enabled admin user on this Mountain Lion Mac.
Using fdesetup on Mountain Lion, fv2admin can enable other non-enabled users like the fv2user account.
fv2admin can enable its own account by being both the authorizing account and the account being enabled.
Mavericks
In Mavericks, fdesetup now prevents non-enabled admin users from enabling other non-enabled users.
On a Mavericks Mac, fv2admin gets an authorization error when trying to enable the fv2user account.
fv2admin can also no longer enable itself.
That said, if your encrypted Mavericks Mac has a personal recovery key available, the personal recovery key can be used to authorize non-enabled accounts.
In the case of the example below, this Mavericks Mac is set up with a personal recovery key. Using fdesetup on Mavericks, the fv2admin account can use sudo to run fdesetup and enable other non-enabled users by entering the personal recovery key when prompted for a password or recovery key.
Another approach to enable non-enabled admin accounts is the following:
1. Log in at the OS login window as the non-enabled admin account
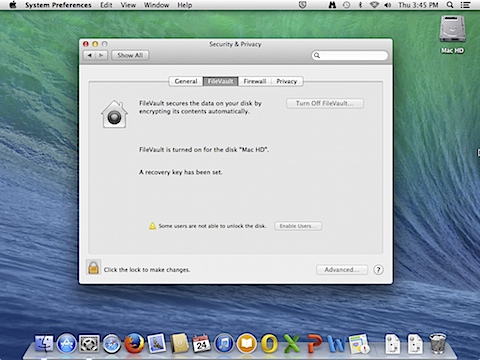
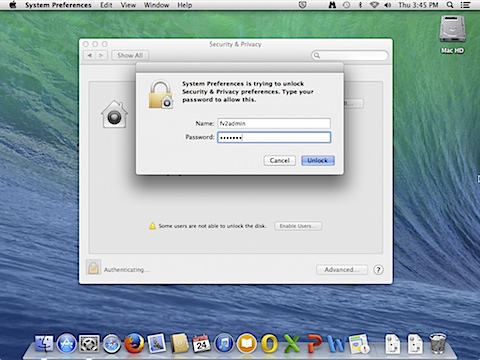
2. Open System Preferences and go to the FileVault preference pane
3. Click the lock to unlock the preference pane and authenticate when prompted.
4. Click the Enable Users button in the preference pane
5. The previously non-enabled admin user account will appear with a green checkbox to show that the account has been enabled.
This approach has worked since FileVault 2 was first introduced in Lion and it continues to work in Mavericks.











Is there a way to programmatically add FV2 enabled users in Mavericks? We would want to script this and not have to add them via your GUI method.
If your Mavericks Mac has an alphanumeric individual recovery key, you can use the individual recovery key in situations where you don’t have an enabled user’s password available.
If you have access to either an enabled account’s password or an individual recovery key, you can build a script to enable other users using fdesetup and a plist file.
I assume since you specifically say “an individual recovery key” the ability to use an institutional key to add users is still broken?
Right, you can’t add users using the institutional key.
That said, you can use fdesetup changerecovery to add an individual recovery key. fdesetup changerecovery allows for the use of the institutional key as authentication, so you could do something like this:
1. Use fdesetup changerecovery to add an individual recovery key to your Mac.
2. Use the newly-created individual recovery key to add your user(s)
3. (Optional) Remove the individual recovery key using fdesetup removerecovery. You can use the newly-created individual recovery key to authenticate the removal, so it authenticates for its own removal.
Once authenticated, the newly-created individual recovery key would then be removed from the system and no longer work.
So adding the individual key does not remove the institutional one? That’s nice. Had no idea you could have both types at once.
fdesetup in Mountain Lion added the capability of having both kinds of recovery key on one encrypted Mac. That capability remains in Mavericks.
See the “Enabling FileVault 2 encryption using one or multiple recovery keys” section here, along with the “Managing individual and institutional recovery keys” section:
Was just reading that! Thanks as usual for all of your expertise on this subject!