Re-syncing local account passwords and Secure Token on FileVault-encrypted Macs running macOS Mojave
As part of FileVault on Apple File System, Apple introduced a new account attribute called Secure Token. As mentioned in a previous post, Secure Token can present some interesting problems for Mac admins who work with FileVault-encrypted laptops. Among the potential complications are these scenarios:
- “I changed the password for my local account, but only the old password is being taken at the FileVault login screen.”
- “We’ve lost the password to the only local user account with a Secure Token, so now we can’t enable any other accounts on this Mac for FileVault.”
Usually, this happens because the local account password in question was changed outside of the Users & Groups preference pane in System Preferences and now Secure Token and the account password are out of sync with each other.
Up until the past few days, the only fix I knew of for that situation was to back up the data and wipe the drive. However, it looks like there is a workaround for encrypted Macs which fixes the password problem and sorts out Secure Token in these scenarios. In both cases, a personal recovery key will be needed as the way to authorize the needed changes. For more details, please see below the jump.
Note: The methods described below only work with local accounts. Mobile accounts need to have password changes authorized by their parent directory service and directory services like Active Directory and Open Directory will not be accessible when using the tools and procedures described below.
There are two methods which can be used with a personal recovery key to reset a local account’s password and resync a Secure Token:
- FileVault login screen password reset
- macOS Recovery password reset
FileVault login screen password reset
At the FileVault login screen, the following procedure can be used to reset a local account’s password:
1. Select the user account in question.
2. Click the question mark icon.

3. Click the arrow icon.

4. Enter the personal recovery key in the provided blank, then click on the arrow icon.

The encryption will unlock at this point and the Mac will boot.

5. At the Reset Password dialog window, enter a new password and then click the Reset Password button.

As part of the password reset process, the Secure Token attribute for the account will also resync. That should allow FileVault to work normally again.
macOS Recovery password reset
In macOS Recovery, there is a resetFileVaultpassword tool which can use the personal recovery key to authorize password changes and Secure Token resync. The following procedure can be used to reset a local account’s password:
1. Boot to macOS Recovery.

2. Under the Utilities menu, select Terminal.

3. In Terminal, enter the following command and hit Enter.
resetFileVaultpassword

This will launch a Reset Password window, with a blank for entering the personal recovery key.

4. Enter the personal recovery key, then click the Next button.

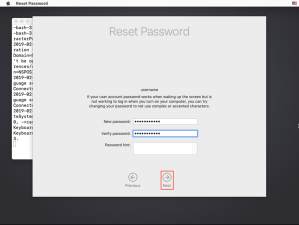
5. Select the account whose password needs to be reset, then click the Next button.

6. Enter a new password and verify it, then click the Next button.
7. When prompted, click the Restart button.
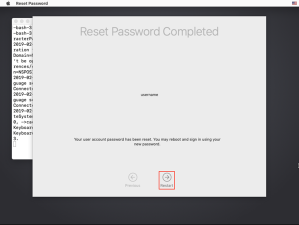
As part of the password reset process, the resetFileVaultpassword tool also resyncs the Secure Token attribute for the account. That should allow FileVault to work normally again.
Nice, I didn’t know about that feature in Recovery. The fix I posted in self-service involves revoking and reissuing securetoken, then updating the apfs preboot volume. That’s consistently resolved the pw mismatch at my org. https://github.com/ducksrfr/mac_admin/blob/master/scripts/Mojave_FileVault_Sync.sh
Hi Stephen,
Your script is quite interesting. I guess this means the device has to have an existing local admin that has secure token already?
I tried running resetFileVaultpassword from recovery, but it wanted my iCloud login and would not go to the individual recovery key screen. Using resetpassowrd in stead eventually brought me to the screen that asked for the individual recovery key. I’m on macOS 10.14.3.
This is what I was seeing as well, Thanks
You can also use Terminal to reset an out of sync FileVault password. Once they are back in sync a normal Password change should keep it in sync:
Enter the following commands:
sudo fdesetup list
• note the UUID of your user (should be a string like 3730F99B-ADAD-468F-B8FB-0D237531A770)
sudo diskutil list
• make note of the Disk Identifier for “Macintosh HD” (should be disk1s1 but may be different)
sudo diskutil apfs changePassphrase disk1s1 [or whatever your actual disk identifier is] -user [UUID]
• enter your current FileVault Password
• change it to your current login password
In our environment, we have a local admin account that is the first account created.For the affected mobile managed accounts,I’ve been logging in with the local admin account and deleting the affected user account in the Users and Groups System Preference Pane and selecting the option not to change the home folder. Then, I log out of the admin account and have the user log in with their correct password. It then prompts me to enable secureToken for that account, with admin credentials.I then, log out, log back in as admin, delete the new home folder, delete the (deleted) from the old home folder, and have the user log back in. In our situation, this has been working
I am doing the same with deleting the User’s account. It seems to clear everything up quickly. However, these are AD accounts so they must come back to campus which is not easy with everyone telecommuting these days.
Rich, in your fixes, does it have to be the Personal recovery key or can it be an institutional one?