Decrypting an APFS encrypted volume using diskutil on macOS 10.13.2
Apple has made changes as of macOS 10.13.2 to the way you can turn off APFS encryption when using the diskutil apfs decryptVolume command.
On macOS 10.13.0 and 10.13.1, an APFS encrypted volume could be decrypted using the following procedure:
- Identify the relevant encrypted APFS volume
- Unlock the encrypted APFS volume
- Decrypt the encrypted APFS volume
Once the drive has been unlocked, you could then decrypt the APFS volume using the command shown below:
diskutil apfs decryptVolume /dev/apfs_volume_id_here
As long as you were using root or admin privileges to run the command, no additional authentication was required to decrypt an unlocked encrypted volume.

However, the diskutil apfs decryptVolume command has been updated on macOS 10.13.2 to require additional authentication:
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| decryptVolume volumeDevice [-user disk | existingCryptoUserUUID] [-passphrase existingPassphrase | -stdinpassphrase] | |
| Start "background" decryption of a currently-encrypted APFS Volume. | |
| The APFS Volume must be unlocked before beginning this operation. | |
| In most cases, you will have to specify some (any) existing cryptographic user and passphrase on the APFS | |
| Volume. If you do not supply a user, the "Disk User" is assumed. If you do not supply a passphrase yet one | |
| is required, you will be prompted interactively. | |
| Ownership of the affected disks is required. |
In order to decrypt using a user account’s password or personal recovery key (PRK), it is necessary to specify the following:
- The relevant user UUID
- The relevant account password or the PRK.
Note: As of macOS 10.13.2, it is not possible to decrypt an encrypted APFS volume using an institutional recovery key (IRK). You can unlock an encrypted APFS volume using an IRK, but diskutil apfs decryptVolume does not include functionality for using an IRK to authenticate the decryption of an encrypted APFS volume.
For more details, please see below the jump.
If you are planning to use a user account’s password to decrypt, you will first need to correctly identify the relevant encrypted APFS volume and which UUID you want to use.
In this case, we’ll be using the following APFS volume identifier:
/dev/disk1s1

The other assumption is that the encrypted APFS volume has been unlocked and is ready for decryption.
If you are booted from the encrypted drive, you can get the UUID of a user account by running the command shown below and matching which UUID belongs to the account you want to use.
fdesetup list

If you are not booted from the encrypted drive, there is another way to get the UUID by running the command shown below and looking at the entries listed as Local Open Directory User. However, this method will not display the account name and may require some guesswork if there is more than one FileVault enabled account enabled.
diskutil apfs listcryptousers /dev/apfs_volume_id_goes_here
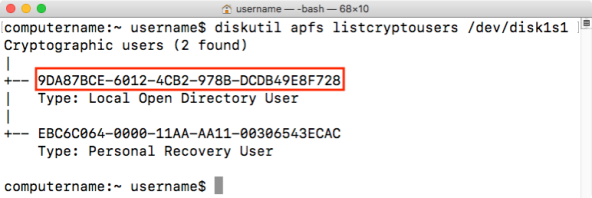
Once you have access to the UUID and password of one of the enabled accounts on the encrypted APFS volume, you can unlock using the command below. You will be prompted to provide the password:
diskutil apfs decryptVolume /dev/apfs_volume_id_goes_here -user uuid_goes_here

If you want to use the PRK, the PRK has its own UUID which only appears if you run the following command:
diskutil apfs listcryptousers /dev/apfs_volume_id_goes_here
In this case, use the UUID associated with the Personal Recovery User entry.

If you have access to the PRK associated with the encrypted APFS volume, you can decrypt using the command below. You will need to provide the relevant UUID and the alphanumeric personal recovery key as part of the command.
diskutil apfs decryptVolume /dev/apfs_volume_id_goes_here -user uuid_goes_here -passphrase personal_recovery_key_goes_here

To show the process of decrypting an unlocked encrypted APFS volume while using a personal recovery key, please see below for a video:
Many many thanks! It worked for me!
and what do I need to do if the encryption is not finished yet? Got the error “is already decrypting or encrypting (-69573)
So any updates on using a IRK to decrypt 10.13.4? since the authentication issue on 10.13.2 “diskutil decryptVolume disk2s1”? This is in reference to the drive already being unlocked using an Instituional Recovery Key – or is there a way to add a user or recovery using the IRK?
Yes here an update
With Version 10.13.3 you will get an error using IRK when running “diskutil apfs decryptvolume” -> Error starting background decryption of APFS Volume: APFS Volume decryption failed to begin (-69595)”
With Version 10.13.4 you will get an error using IRK when running “diskutil apfs decryptvolume” -> Error starting background decryption of APFS Volume: Passphrase incorrect (-69550)”
I will try to encrypt in 10.13.4 and will try again to decrypt (maybe a bug during encryption with 10.13.3?)
Having the same issue as you Roberto, and for me 10.13.4 did not resolve nor did it allow me to decrypt.
I am, unfortunately experiencing the same on a volumen encrypted on 10.13.4, Roberto.
Same as you. How have you solved it?
Thanks so much for this! It’s an excellent article with a good, clear writing style too.
Why is my status seemingly stuck at 10%?
Thanks so much for this! It’s an excellent article
I am stuck at 10% as well. How did you fix it?
Thanks a lot!!!
Has anybody been able to successfully resume progress of decryption when it is stuck at 10%? Seems the only way to “resolve” it is to reinstall the OS.
I’m having the same problem buddy
Thank you!
Ooh man you saved so much of my time. I am very greatful!
excellent! you solved my problom! thanks a lot! 🙂 so happy
Thank you very much for your detailed instructions. Saved me from hours of work.
I have a strange problem, hoping someone can help. When I run “diskutil apfs listcryptousers” I only get the “iCloud Recovery User” and the “iCloud Recovery External Key”. There is no “Local Open Directory User”. When I use resetpassword from the recovery mode terminal, I am able to use iCloud to unlock the disk and I can see the two user accounts. Those accounts are in the Open Directory however are not file vault cryptousers on the disk. This happened after an attempted upgrade to Mojave. Suggestions? I have tried “diskutil apfs updatePreboot” and so many other things based on extensive research. It seems file vault somehow forgot about these users. I can’t seem to find a way to decrypt the drive with the iCloud users (it prompts for a passphrase but the passphrase I set using resetpassword does not work, nor does the iCloud password. I also can’t find a way to add a user from the recovery mode. I cannot enter single user mode. Can’t boot, goes right to prohibited screen (which seems to be because it can’t find any accounts).
Having the exact same issue as you while trying to recover my buddy’s laptop. His did an update to Mojave but has no Local Open Directory Users’. Any luck for you?
Has anybody been able to successfully resume progress of decryption when it is stuck at 10%? Seems the only way to “resolve” it is to reinstall the OS.
if you have something “paused” in encryption/decryption, just enter it in terminal (recovery)
/usr/libexec/apfsd for apfsl file system
So just an FYI, Catalina has broken the ability to use terminal to perform any recovery steps (I was on with Business support for hours to no avail).
If you have filevault enabled it boots to recovery assistant which asks for the password of a user with filevault acces. Any which way you boot goes to this useless screen if you don’t have a password (Catalina recovery, internet recovery, USB media) – which as we know sometimes filevault and user passwords can get out of sync. So I was unable to decrypt without a terminal..
Made a bootable usb of Mojave and could get to terminal. Then unlocked and decrypted using the diskutil commands.
Thanks for the guides.
Using macOS 10.14.5 I want to decrypt an APFS in an Image from a non-T2 system and get
Error starting background decryption of APFS Volume: APFS Volume decryption failed to begin (-69595)
The password is correct, because If I enter a wrong password, I get a different error.
hdiutil attach -nomount Image.dd
diskutil apfs unlockVolume /dev/diskXs1
diskutil apfs decryptVolume /dev/diskXs1 -user %UUID%
(and no, I don’t use an IRK)
using encripted APFS make my HDD External slow, hope without encryption will make it fast.
but not secure 😦
Thank you
Hi everybody!
To decrypt your hackintosh’s drive – you have two options.
FIRST WAY:
You need install FileVault drivers into your EFI configuration, use this instruction below!
https://ihackline.com/2020/10/05/filevault-hackintosh/
You have to made some changes to ENABLE natively FileVault on hackintosh to use your drive encryption normally.
SECOND WAY:
USE your RECOVERY partition to start decrypting process.
0) BOOT INTO RECOVERY PARTITION (cmd+R when booting) or load into clean system from external drive:
1) open terminal from recovery utilities
2) FOR APFS DRIVE type:
/usr/libexec/apfsd
OR TRY THAT!
sudo /usr/libexec/apfsd
FOR HFS DRIVE:
/usr/libexec/corestoraged
OR TRY THAT!
sudo /usr/libexec/corestoraged
3) TO RESUME/START decrypt/encrypt SERVICE of your drive:
OPEN NEW terminal’s window.
4) TYPE:
diskutil apfs list
see your main drive disk0s0 (for example) and write its UUID
5) TYPE:
diskutil apfs listcryptousers /dev/disk0s0
see your username
6) TYPE:
diskutil apfs decryptVolume /dev/disk0s0 -user uuid_goes_here -passphrase 1234567890
Remember!
“1234567890” – is your password of user
“uuid_goes_here” – UUID of your drive
“disk0s0” – your drive partition
7) Check your decrypting status:
diskutil apfs list
P.S. Decryption will be very long. Even if it’s an SSD. Most importantly, check that the decryption percentages are slowly but increasing.
Good luck!