Archive
Slides from the “OS X Security – Defense in Depth” Session at JAMF Nation User Conference 2015
For those who wanted a copy of my security talk at JAMF Nation User Conference 2015, here are links to the slides in PDF and Keynote format.
Configuring System Integrity Protection without booting to Recovery HD
One interesting part of Apple’s developer documentation for System Integrity Protection (SIP) is the note shown below, indicating that it’s possible to configure SIP for environments that can’t access Recovery.

When I followed up with Apple about this, I was told that this meant I could configure it using NetBoot, using a NetBoot set that included the needed Recovery environment.
The example used was leveraging a new option in System Image Utility to create a package-only installation NetBoot set.

This new type of NetBoot set is is designed to install only scripts, configuration profiles and packages as opposed to installing an OS. For more details, see below the jump.
System Integrity Protection – Adding another layer to Apple’s security model
As part of the release of OS X El Capitan, Apple has added a new layer named System Integrity Protection (SIP) to its security model. To understand how System Integrity Protection fits in, let’s first take a look at Apple’s security model as it existed as of OS X Yosemite.
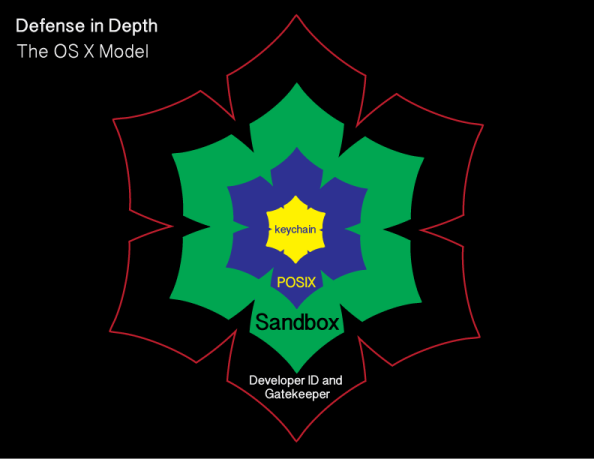
Gatekeeper is one of the outer lines of defense. It allows users to restrict which sources they can install applications from, with the general idea being that malware will not be from an allowed source.
OS X also uses sandboxing extensively. A sandbox typically provides a tightly controlled set of resources for programs to run in. Network access, the ability to inspect the host system, or reading from input devices is usually disallowed or heavily restricted.
OS X uses the Unix permissions model as defined by POSIX, which governs which users and groups can access which files and directories. If a particular user account requests access to a particular file or directory and does not have the necessary rights, that account is refused access.
The innermost layer of defense are keychains. Keychains are very specialized databases which are designed for the storing of secrets, like passwords, private keys, PIN numbers, and then controlling access to those secrets. To help protect these secrets, keychains are encrypted.
There’s an issue with this model though and it’s been there for decades. It pre-exists OS X and even pre-exists Apple as a company. That issue is found in the POSIX permissions layer.

Root

Root is the superuser for a Unix system and the Unix permissions model is designed around the assumption that root has access to everything. Apple has not ignored this issue and has put some controls in place to limit the actual root user. These controls include disabling the root user account, discouraging its use, and providing ways to access elevated or root privileges using other means.
However, the root user account is still present and still can do anything on the system.
System Integrity Protection
To limit what the superuser can do and add another layer to OS X’s security model, Apple has developed SIP and deployed it as part of OS X El Capitan. SIP is designed to limit the power of root and to protect the system even from the superuser. For more details, see below the jump.
System Integrity Protection and resetting NVRAM
OS X El Capitan’s new System Integrity Protection (SIP) security feature stores its active security configuration in NVRAM. This allows SIP’s configuration to persist across OS installs, but this design choice also means that resetting NVRAM will cause SIP to reset as well. In my testing, this reset will result in the following SIP configuration:
- SIP will be enabled with all protections in place
- No entries will be set in the SIP NetBoot whitelist
Resetting the NVRAM, otherwise known as a PRAM reset or PRAM zap, has been a standard part of the Mac troubleshooting toolkit for a long time and is performed by pressing and holding down the Option, Command (⌘), P, and R keyboard keys at startup.

For shops that do not plan to change SIP’s default configuration or set a NetBoot whitelist, NVRAM resets causing SIP’s configuration to also reset should not affect normal operations.
However, for those shops who will need to maintain a NetBoot whitelist or a custom SIP configuration, I would advise education where needed about this change and how it affects SIP configuration in your environment.
System Integrity Protection and the end of XProtect management for browser plug-ins
OS X El Capitan adds a new security feature named System Integrity Protection (SIP). Among other things, SIP prevents parties other than Apple from adding, deleting or modifying directories and files stored in certain directories:
- /bin
- /sbin
- /usr
- /System
Apple has indicated that the following directories are available for developers to access:
- /usr/local
- /Applications
- /Library
- ~/Library
All directories in /usr except for /usr/local are protected by SIP.
SIP’s protection of /System affects XProtect’s XProtect.plist and XProtect.meta.plist configuration files as they are stored in the following location inside /System:
/System/Library/CoreServices/CoreTypes.bundle/Contents/Resources/XProtect.plist
/System/Library/CoreServices/CoreTypes.bundle/Contents/Resources/XProtect.meta.plist
As the XProtect configuration files will be locked against editing on OS X El Capitan, this means that they can no longer be managed to allow older versions of the Flash and Java browser plug-ins to run.
If your shop includes a mission-critical system that requires using older Flash or Java browser plug-ins, I recommend working with your vendor and/or in-house developers to find out:
- If the use of the Java and/or Flash browser plug-ins can be discontinued.
- If their use can’t be discontinued, if the system in question can be updated to support the latest versions of these plug-ins and continue to be compatible as new versions of the Java and/or Flash browser plug-ins are released.
Update – 9-14-2015: Josh Dyson has pointed out that there is a way to allow older plug-ins to access specific sites.
By adding the needed sites to a whitelist in Safari and setting those specific sites to Allow Always, those sites’ functions will be accessible with the older browser plug-in even if XProtect would otherwise block the use of the plug-in. Websites not included in the whitelist would still have the use of the plug-in blocked.
Apple has provided a KBase article showing how to manage Safari plug-in options, including how to whitelist websites, using a configuration profile. It’s available via the link below:
NetBooting and System Integrity Protection
Apple took an unusual step this week and released a knowledgebase (KBase) article that refers to an as-yet unreleased operating system:
Prepare for NetBoot, NetInstall, and NetRestore requirements in OS X El Capitan
I can only praise the decision to create it. The content covered affects a number of enterprise Mac environments and gives the Mac admins who support those environments time to prepare for an important change which may affect them.
That said, the KBase article itself is confusingly written and also includes an error. For more details, see below the jump.

Recent Comments