Clearing the logged-in Microsoft SSO user on macOS using Microsoft’s Company Portal app
As part of working on a task recently, I ran into an issue with Microsoft’s Enterprise SSO plug-in on macOS. This plug-in enables single sign-on for Entra ID accounts for applications which support it. In this case, the issue was the following:
Desired behavior:
- Open application.
- Click the login button.
- Be prompted for the Entra ID user account to sign in with.
- Log in with that user account.
Actual behavior:
- Open application.
- Click the login button.
- Be automatically logged in as the Entra ID user registered for single sign-on.
Unfortunately for my use case, I really needed to have the application in question prompt the user for which account they needed to log in with because a user account other than the one registered for single sign-on needed to be able to sign in to the application in question.
After some discussion in the #jamf-intune-integration channel in the Mac Admins Slack, I was pointed towards a way to sign out the account which was enabled for single sign-on using Microsoft’s Company Portal application. With no account enabled for single sign-on, the application would now prompt for a user account to sign in with. For more details, please see below the jump.
To sign out the Entra ID account enabled for single sign-on using the Company Portal application, please use the procedure described below:
1. Open the Company Portal application.

2. Sign into the Company Portal application as the user of the computer.
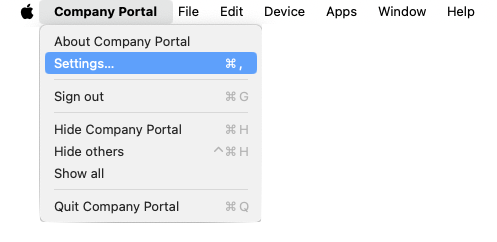
3. Under the Company Portal menu in the menubar, select Settings…
4. In the Settings window, in the Single sign-on (SSO) section, click the Remove account from this device button.
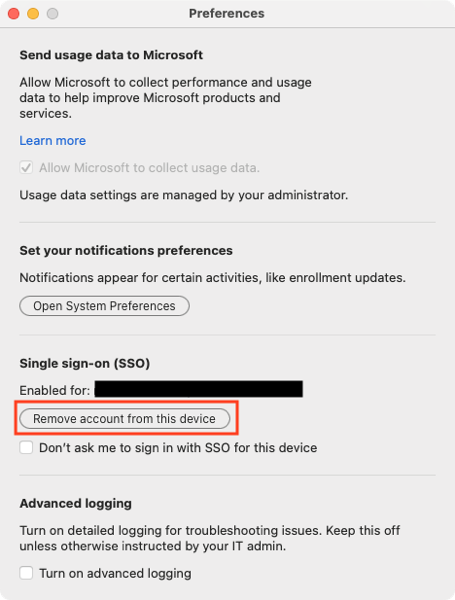
Note: I’ve noticed that clicking the Remove account from this device button doesn’t make a noticeable change in the Settings window; the account still appears as enabled. However, clicking the button should do what’s needed and applications should now prompt for a user account.
Hi Rich, did you maybe try and add the app to the blocked list of the Microsoft SSO extension? Described here: https://learn.microsoft.com/en-us/entra/identity-platform/apple-sso-plugin#disable-sso-for-specific-apps
A couple thoughts:
1. Using keychain access to find (and remove) any “primaryrefresh” entries as described here has the same effect in my testing on Sonoma 14.3.1 (Company Portal 5.2312.7): https://learn.microsoft.com/en-us/entra/identity/devices/troubleshoot-mac-sso-extension-plugin?tabs=flowchart-macos#checking-keychain-access-for-prt
2. If you use MS Edge to create multiple profiles you can have multiple PRT’s stored for the SSO Extension causing a prompt for verification every time the SSO PRTs are engaged (ie when signing into a new application federated with Entra ID/Azure AD in Safari)