Whitelisting third-party kernel extensions using profiles
As part of macOS 10.13.2, Apple introduced the concept of User Approved MDM Enrollment (UAMDM). UAMDM grants mobile device management (MDM) additional management privileges, beyond what is allowed for macOS MDM enrollments which have not been “user approved”.
As of macOS 10.13.4, the only additional management privilege associated with UAMDM is that it allows you to deploy a profile which provides a whitelist for third-party kernel extensions. This profile allows a company, school or institution to avoid the need to have individual users approve the running of approved software.
Without the profile, third-party kernel extensions will need to be approved through the User-Approved Kernel Extension Loading (UAKEL) process. Here’s how that process looks:
1. When a request is made to the OS to load a third-party kernel extension which the user has not yet approved, the load request is denied and macOS presents an alert to the user.

2. The alert tells the user how to approve the loading of the kernel extension signed by a particular developer or vendor, by following this procedure:
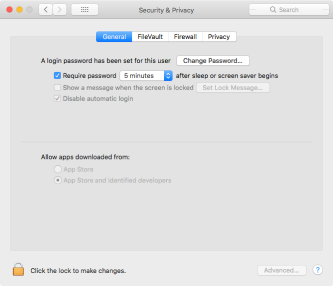
A. Open System Preferences
B. Go to the Security & Privacy preference pane

C. Click the Allow button.

Note: This approval is only available for 30 minutes. After that, it disappears until the following happens:
i. The Mac restarts
ii. Another attempt is made to load the kernel extension.
While waiting for the kernel extension to be approved, a copy of the kernel extension is made by the operating system and stored in the following location:
/Library/StagedExtensions
Once approved, another copy of the kernel extension is made and allowed to load.

This process is relatively easy for an individual to manage on their own computer, but it would be very difficult to manage when dealing with more than a handful of Macs. To help companies, schools and institutions, Apple has made a management profile option available to centrally approve third-party kernel extensions. For more details, please see below the jump.
To help whitelist all kernel extensions from a particular vendor or whitelist only specific ones, Apple has made two sets of identifying criteria available:
- Team Identifier
- Bundle Identifier
Team Identifier
A team identifier is a alphanumeric string which appears similar to the one shown below:
7AGZNQ2S2T
It appears to use a developer or vendor’s Developer ID for Signing Kexts certificate identifier. This certificate would be used by a developer or vendor to sign all or most of their kernel extensions.
Whitelisting using the Team Identifier has the advantage of being able to whitelist multiple third party kernel extensions from a specific developer or vendor. This capability allows Mac admins to identify a particular developer or vendor as being trusted in their environment and have all of the relevant kernel extensions be allowed to load by the whitelist.
Note: The UAKEL process appears to use team identity when approving kernel extensions, which potentially allows multiple kernel extensions to be approved at once.
Bundle Identifier
The Bundle Identifier is specific to a particular kernel extension. It is contained in the Info.plist file stored inside each kernel extension.

Whitelisting using the bundle identifier allows the Mac admin to get very granular about which kernel extensions from a specific developer or vendor are approved and which are not. If using the bundle identifier as part of the whitelist, both the Team Identifier and the Bundle Identifier need to be specified in the profile.
To help Mac admins, a community-written Google Doc spreadsheet is available here which lists various team identities and their associated bundle identifiers:
https://docs.google.com/spreadsheets/d/1IWrbE8xiau4rU2mtXYji9vSPWDqb56luh0OhD5XS0AM/edit?usp=sharing
(Hat tip to Contains_ENG for creating the document and developing a script to detect the relevant kernel extension info.)
Using Team Identifier by itself in a third-party kernel extension whitelist profile
If you want to use only the Team Identifier when whitelisting kernel extensions, the profile should be written as shown below:
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| <?xml version="1.0" encoding="utf-8"?> | |
| <!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"> | |
| <plist version="1"> | |
| <dict> | |
| <key>PayloadUUID</key> | |
| <string>40C19D5B-76D7-4C1C-BC9D-2F7EB29CFF4D</string> | |
| <key>PayloadType</key> | |
| <string>Configuration</string> | |
| <key>PayloadOrganization</key> | |
| <string>Company Name</string> | |
| <key>PayloadIdentifier</key> | |
| <string>40C19D5B-76D7-4C1C-BC9D-2F7EB29CFF4D</string> | |
| <key>PayloadDisplayName</key> | |
| <string>Approved Kernel Extensions</string> | |
| <key>PayloadDescription</key> | |
| <string>This profile configures your Mac to automatically enable third-party kernel extensions from specified vendors.</string> | |
| <key>PayloadVersion</key> | |
| <integer>1</integer> | |
| <key>PayloadEnabled</key> | |
| <true/> | |
| <key>PayloadRemovalDisallowed</key> | |
| <true/> | |
| <key>PayloadScope</key> | |
| <string>System</string> | |
| <key>PayloadContent</key> | |
| <array> | |
| <dict> | |
| <key>PayloadUUID</key> | |
| <string>98D01A7B-ADC1-43C8-AB8E-8BDC25FCA3C9</string> | |
| <key>PayloadType</key> | |
| <string>com.apple.syspolicy.kernel-extension-policy</string> | |
| <key>PayloadOrganization</key> | |
| <string>Company Name</string> | |
| <key>PayloadIdentifier</key> | |
| <string>98D01A7B-ADC1-43C8-AB8E-8BDC25FCA3C9</string> | |
| <key>PayloadDisplayName</key> | |
| <string>Approved Kernel Extensions</string> | |
| <key>PayloadDescription</key> | |
| <string/> | |
| <key>PayloadVersion</key> | |
| <integer>1</integer> | |
| <key>PayloadEnabled</key> | |
| <true/> | |
| <key>AllowUserOverrides</key> | |
| <true/> | |
| <key>AllowedTeamIdentifiers</key> | |
| <array> | |
| <string>7AGZNQ2S2T</string> | |
| <string>KBVSJ83SS9</string> | |
| <string>VB5E2TV963</string> | |
| </array> | |
| </dict> | |
| </array> | |
| </dict> | |
| </plist> |
On the individual Macs which receive the profile, it should show up looking similar to this:


Using Team Identifier and Bundle Identifier in a third-party kernel extension whitelist profile
If you want to use both Team Identifier and Bundle Identifier when whitelisting specific kernel extensions, the profile should be written as shown below:
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| <?xml version="1.0" encoding="utf-8"?> | |
| <!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"> | |
| <plist version="1"> | |
| <dict> | |
| <key>PayloadUUID</key> | |
| <string>9BF0A852-EF1F-45FD-939B-A70CD4329F4C</string> | |
| <key>PayloadType</key> | |
| <string>Configuration</string> | |
| <key>PayloadOrganization</key> | |
| <string>Company Name</string> | |
| <key>PayloadIdentifier</key> | |
| <string>9BF0A852-EF1F-45FD-939B-A70CD4329F4C</string> | |
| <key>PayloadDisplayName</key> | |
| <string>Approved Kernel Extensions</string> | |
| <key>PayloadDescription</key> | |
| <string>This profile configures your Mac to automatically enable third-party kernel extensions from specified vendors.</string> | |
| <key>PayloadVersion</key> | |
| <integer>1</integer> | |
| <key>PayloadEnabled</key> | |
| <true/> | |
| <key>PayloadRemovalDisallowed</key> | |
| <true/> | |
| <key>PayloadScope</key> | |
| <string>System</string> | |
| <key>PayloadContent</key> | |
| <array> | |
| <dict> | |
| <key>PayloadUUID</key> | |
| <string>9B77518B-65E3-47D8-B75C-7567953C6466</string> | |
| <key>PayloadType</key> | |
| <string>com.apple.syspolicy.kernel-extension-policy</string> | |
| <key>PayloadOrganization</key> | |
| <string>Company Name</string> | |
| <key>PayloadIdentifier</key> | |
| <string>9B77518B-65E3-47D8-B75C-7567953C6466</string> | |
| <key>PayloadDisplayName</key> | |
| <string>Approved Kernel Extensions</string> | |
| <key>PayloadDescription</key> | |
| <string/> | |
| <key>PayloadVersion</key> | |
| <integer>1</integer> | |
| <key>PayloadEnabled</key> | |
| <true/> | |
| <key>AllowUserOverrides</key> | |
| <true/> | |
| <key>AllowedKernelExtensions</key> | |
| <dict> | |
| <key>7AGZNQ2S2T</key> | |
| <array> | |
| <string>com.bit9.cbsystemproxy</string> | |
| <string>com.carbonblack.CbOsxSensorProcmon</string> | |
| <string>com.carbonblack.CbOsxSensorNetmon</string> | |
| </array> | |
| <key>VB5E2TV963</key> | |
| <array> | |
| <string>org.virtualbox.kext.VBoxNetAdp</string> | |
| <string>org.virtualbox.kext.VBoxDrv</string> | |
| <string>org.virtualbox.kext.VBoxNetFlt</string> | |
| <string>org.virtualbox.kext.VBoxUSB</string> | |
| </array> | |
| <key>KBVSJ83SS9</key> | |
| <array> | |
| <string>CitrixGUSB.kext</string> | |
| <string>com.citrix.kext.gusb</string> | |
| </array> | |
| </dict> | |
| </dict> | |
| </array> | |
| </dict> | |
| </plist> |
On the individual Macs which receive the profile, it should show up looking similar to this:


If you’re using Jamf Pro to deploy a third-party kernel extension whitelist profile profile, it should appear as a built-in profile option. Here’s how it should appear if using only team identifiers:
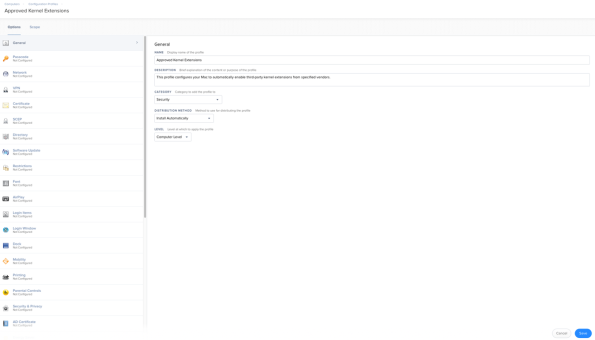

If using both team identities and bundle identifiers:


Thank you for this.
This is great information, with these profiles does this still require a MDM solution ? Can it be used even if your institution does not have an MDM but does have a management tool/utility?
An MDM solution and user-approved MDM is a requirement for deploying third party kernel extension whitelist profiles.
Any chance you could do a write-up on how to apply a .mobileconfig with a kernel white list using Munki?
Applying a .mobileconfig with a kernel whitelist requires the use of an MDM server. This is an Apple-mandated requirement for the kernel extension whitelist profile.
great article thank you !! also have a question, is it possible to update existing CP with whitelisted kext files, like adding teamids to an existing CP that is already rolled out using Jamf ?
Very helpful, thank you!
Thank you for this. I have a question, though: My company has not yet migrated to Jamf Pro 10, we’re still on Casper 9.101. I’ve been trying to reverse-engineer a config profile utilizing your xml data for whitelisting by Team ID, set as a custom payload. So far it’s not working (all the directives get deployed to the client machines, but they’re all out of order; is that why? When a supposed-to-be-whitelisted KEXT loads, I still get the alert requesting approval.) Do you know of any way to make this same thing work while being deployed from Casper 9.101?
Never mind. Upon further research I believe I’ve answered my own question. It isn’t possible without native support for the specific config profile payload being built into the MDM system. Jamf Pro 10 has this. I’ll just have to light a fire in attempting to accelerate my company’s adoption of Jamf Pro 10.
Super helpful as ever -thanks!
Hi Rich, this is wonderful. We were noticing some problems with Mojave. Are any extra steps necessary? Thank you
So, Toast Titanium…… Roxio have NO_TEAM_ID.. Only an identifier… How do you go about whitelisting this??
Hi, great as usual…
I also have a question: How do I check the kext is approved after the deployment of the CP?
With something like kextfind?
Do the payloads HAVE to be signed by a CA?
As I learn and test, I’m trying to create a simple .mobileconfig using macOS server locally, and apply it to another macbook by simply manually installing it (I’m just moving it between machines via dropbox for now).
I’m 99% sure the file was configured properly, but when I attempted to install virtualbox after installing the profile, I still received the System Extension Blocked notice.
here’s my mobileconfig dropped into a google sheet:
https://docs.google.com/spreadsheets/d/1-2zrC8cn_5eUs-q3IpzZ_XAm_e32y3NywJRy7z2h_WQ/edit?usp=sharing
The only thing I can think of is that it’s not signed.