Unlocking or decrypting a FileVault 2-encrypted Fusion Drive from the command line
Unlocking or decrypting a FileVault 2-encrypted Fusion drive from the command line can be a little different from how you would handle a non-Fusion drive. This is because Apple has created Fusion drives by using the Core Storage volume manager that they first introduced in OS X 10.7.x. Normally when you enable FileVault 2, there is not an existing Core Storage volume on the drive being encrypted and the FileVault 2 process creates it. When a drive is decrypted using the diskutil cs revert command, that CoreStorage volume is then removed as part of the process.
However, with Fusion drives, not only is there an existing CoreStorage volume present before encryption, you want to make sure it’s not being removed as part of the decryption process. Doing so would destroy the Fusion drive setup and potentially result in the loss of all data stored on the Fusion drive.
There’s two tools that you can use to safely decrypt a Fusion drive on OS X Mavericks:
fdesetup
fdesetup includes the disable verb, which turns off FileVault 2 encryption on a FileVault 2-encrypted Mac. To decrypt using fdesetup, run the following command with root privileges:
fdesetup disable
You’ll be prompted for the password of an account that’s authorized to unlock the encryption, or the personal recovery key if available. Once provided, decryption of the encrypted volume will begin. One limitation of using fdesetup to decrypt is that you’ll need to be booted from the same boot drive that you want to decrypt, as you can’t specify a different drive with fdesetup.
diskutil
diskutil is able to decrypt FileVault 2-encrypted drives other than the one you’re booted from, but you’ll need to identify the Logical Volume UUID of the encrypted drive using the following command:
diskutil cs list
Running that command will give you a listing of all Core Storage volumes. To help identify what you’re looking for, I’ve highlighted the UUID of the encrypted drive in this example:
Once you have the UUID, you can then either unlock or decrypt the encrypted volume using the following commands. If the goal is to decrypt, be aware that you’ll need to unlock the drive first.
Using the password of an authorized account on the command line
To unlock, run the following command:
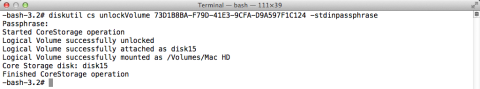
diskutil cs unlockVolume UUID -stdinpassphrase
The -stdinpassphrase flag will cause the command to prompt you for the password of an account that’s authorized to unlock the encryption. If successful, the drive will unlock and mount. You should see output similar to that shown below.
Once you’ve unlocked the disk, you can then decrypt it and return it to being an unencrypted Core Storage volume.
To decrypt, run the following command:
diskutil cs decryptVolume UUID -stdinpassphrase
You’ll be prompted for the password of an account that’s authorized to unlock the encryption. Once provided, decryption of the encrypted volume will begin.
Using the personal recovery key on the command line
If you don’t have the password of any of the authorized accounts and the Mac has a personal recovery key associated with it, you can use the personal recovery key to authorize. The commands are mostly the same, but instead of using the -stdinpassphrase flag, you instead use -passphrase and enter the recovery key.
To unlock, run the following command:
diskutil cs unlockVolume UUID -passphrase recoverykey
If successful, the drive will unlock and mount. You should see output similar to that shown below.
Once you’ve unlocked the drive, you should also be able to decrypt it using this command:
diskutil cs decryptVolume UUID -passphrase recoverykey
Using the institutional recovery key on the command line
Assuming that the FileVault 2 encryption on your Fusion drive is using an institutional key, you can unlock or decrypt the encryption using a FileVaultMaster keychain that contains both the public and private key of your institutional recovery key. One requirement is that you will need to be booted from a Recovery HD partition or from Internet Recovery. Here’s how to do this:
1. Copy the FileVaultMaster keychain that contains both the public and private key of your institutional recovery key to a drive that you can access from Recovery HD.
2. Boot to Recovery HD.
3. Get the Logical Volume UUID of the encrypted drive by running the following command:
diskutil cs list
4. With the UUID information acquired, run the following command to unlock the FileVaultMaster.keychain:
security unlock-keychain /path/to/FileVaultMaster.keychain
Once this command is run, you’ll need to enter the keychain’s password when prompted. If the password is accepted, you’ll be taken to the next prompt.
5. Run the following command to unlock the encrypted Core Storage volume on the encrypted Mac:
diskutil cs unlockVolume UUID -recoveryKeychain /path/to/FileVaultMaster.keychain
6. You should then see output similar to the following:
Once you’ve unlocked the disk, you can then decrypt the encrypted Core Storage volume by running the following command:
diskutil cs decryptVolume UUID -recoveryKeychain /path/to/FileVaultMaster.keychain
Verifying decryption
Once the Fusion drive has been completely decrypted, it should still be listed as a Core Storage volume when diskutil cs list is run. The relevant values to check if a Fusion drive is encrypted or not are these:
Encryption Type:
Conversion Status:
Conversion Direction:
Has Encrypted Extents:
On an encrypted Fusion drive, these values should be like the ones shown below:
Encryption Type: AES-XTS
Conversion Status: Complete
Conversion Direction: -none-
Has Encrypted Extents: Yes
On an decrypting Fusion drive, these values should be like the ones shown below:
Encryption Type: AES-XTS
Conversion Status: Converting
Conversion Direction: backward
Has Encrypted Extents: Yes
On a Fusion drive that has just been decrypted, these values should be like the ones shown below:
Encryption Type: AES-XTS
Conversion Status: NoConversion
Conversion Direction: -none-
Has Encrypted Extents: No
On a Fusion drive that has never been encrypted, or been decrypted then restarted at least once since the decryption finished, these values should be like the ones shown below:
Encryption Type: None
Conversion Status: NoConversion
Conversion Direction: -none-
Has Encrypted Extents: No











So when you have a LVF saying Conversion Status: Converting, Conversion Direction: -none- and Has Encrypted Extents: Yes, then what would you expect it to be doing?
What’s the “Encryption Type” listed as?
Encrytion Type says AES-XTS.
It sounds like it has either finished the encryption process, or (if you’re trying to decrypt), it’s not decrypting.
If you’re trying to decrypt, I recommend doing a shutdown of the system, letting it sit powered-off for a minute or so, then start it back up. Once the system is back up, see if the decryption process is now proceeding.
I was in the process of decrypting the volume. The LV says that it’s done but the LVF still needs unlocking and have the aforementioned properties.
Maybe I should add that the iMac has a home build Fusion drive and I’m running 10.10 beta 1 on it. Or running is maybe a bit of a stretch… Lets just say that I’m looking forward to the final product without bugs 🙂
Hello.
I have the same situation as yours.
I’m running 10.10 PB1, and I have:
Encryption Type: AES-XTS
Conversion Status: Converting
Conversion Direction: -none-
Has Encrypted Extents: Yes
Have you solved the promlem?
If so, could you tell me how to do it?
Thank you.
Just wanted to say that your instructions here for “Using the personal recovery key on the command line” enabled us to perform a data recovery on an end-user’s hard drive that was failing. We performed a block-level clone and suspected the drive wouldn’t boot (which it did not, prompting us for the initial password but then failing to reach login), but even when the drive was connected to an external system it would prompt for the password but then fail indicating the password was incorrect. Attempting to perform this in Disk Utility also failed in the same manner. However, unlocking and decrypting the drive via the command line with diskutil *did* work and enabled us to use the recovery software on the drive to get the user’s profile. Thanks!
Hi, I tried to follow your instruction since I can’t access my main partition anymore. I can unlock the drive but the decryption fail every time. I tried using Disk Utility.app and the command line using decryptVolume on my Fusion Drive but it yield an error -69693 because of an underlying error -536870212. Any idea ?
I have a problem with the unencrypt:
LPRALL-M-F1BC:~ root# diskutil cs unlockvolume 63719040-1D85-4C0B-806E-9D3479342D24 -stdinpasssphrase
63719040-1D85-4C0B-806E-9D3479342D24 is already unlocked and is attached as disk6
LPRALL-M-F1BC:~ root# diskutil cs decryptvolume 63719040-1D85-4C0B-806E-9D3479342D24 -stdinpassphrase
Passphrase:
The Core Storage Logical Volume UUID is 63719040-1D85-4C0B-806E-9D3479342D24
Started CoreStorage operation on disk6 Apple
Error: -69749: Unable to unlock the Core Storage volume
LPRALL-M-F1BC:~ root#
So unlock volume tells me its already unlocked as does list:
+-> Logical Volume Family 80B961A9-F6DE-43D5-898A-79B838DC3FCA
| ———————————————————-
| Encryption Status: Unlocked
| Encryption Type: AES-XTS
| Conversion Status: Complete
| Conversion Direction: -none-
| Has Encrypted Extents: Yes
| Fully Secure: Yes
| Passphrase Required: Yes
| |
| +-> Logical Volume 63719040-1D85-4C0B-806E-9D3479342D24
| —————————————————
| Disk: disk6
| Status: Online
| Size (Total): 729030344704 B (729.0 GB)
| Conversion Progress: -none-
| Revertible: No
| LV Name: Apple
| Volume Name: Apple
| Content Hint: Apple_HFS
|
But decrypt volume tells me it’s unable to unlock the Core Storage volume.
The reason I’m trying to do this is to erase the disk so that I can restore from TimeMachine. There appears to be something wrong with the drive that prevents TimeMachine from doing an erase, and also prevents me from doing an erase, so I thought that it could be FileVault that was causing the problem.
I know this post is older than dirt, but I got myself into a pickle by encrypting my boot drive. I have a not very old backup clone. The main boot disk won’t boot anymore. Trying to decrypt using the instructions I get a message “You can’t decrypt until encryption is finished”
The diskutil cs list command for that fusion LVG shows:
| Encryption Type: AES-XTS
| Encryption Status: Unlocked
| Conversion Status: Converting (forward)
| High Level Queries: Not Fully Secure
| | Passphrase Required
| | Accepts New Users
| | Has Visible Users
| | Has Volume Key